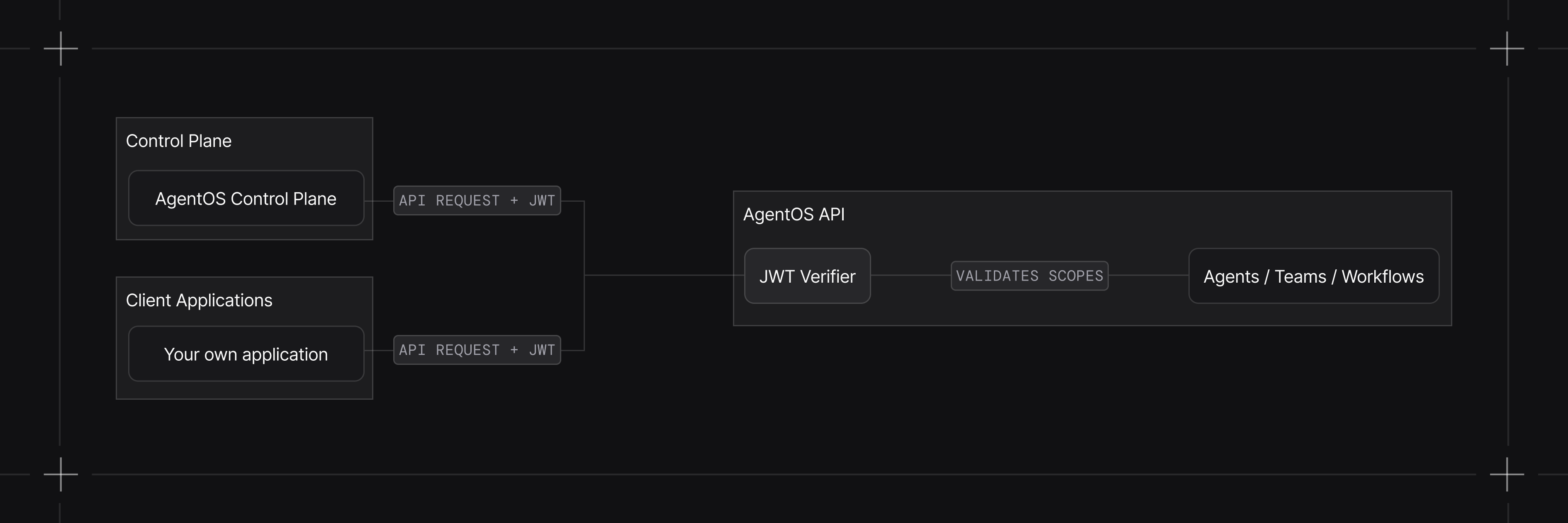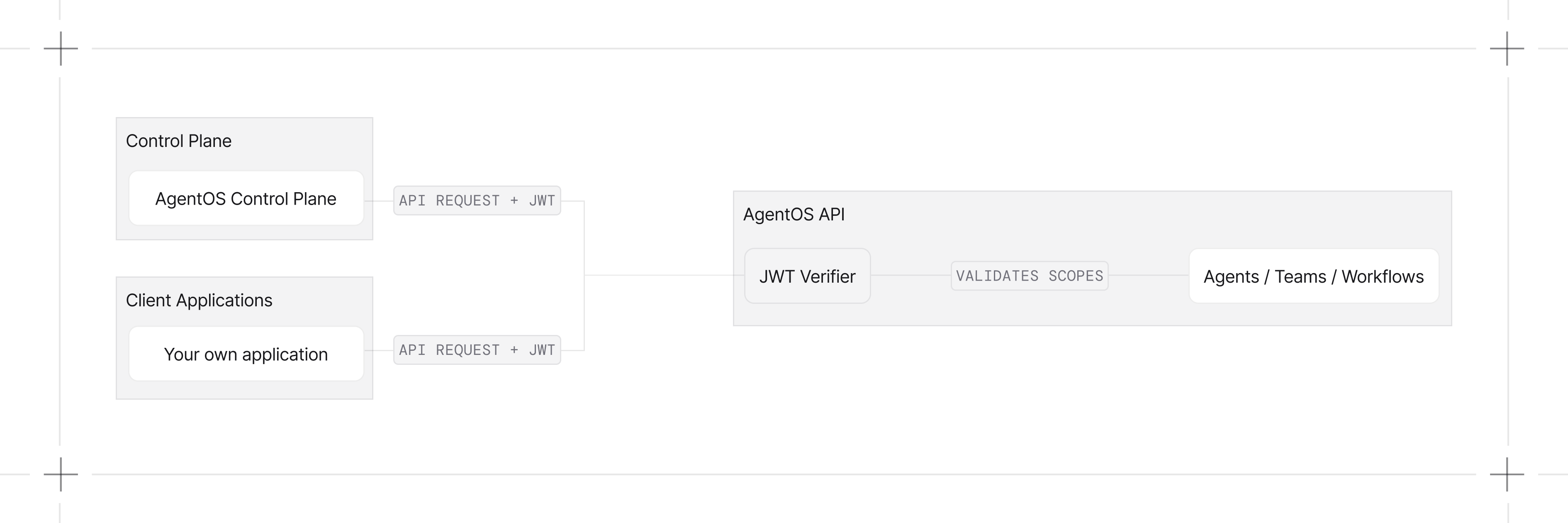
Quick Start
Enable RBAC when initializing AgentOS:JWT_VERIFICATION_KEY environment variable to your public key:
Scope Format
RBAC uses a hierarchical scope format:| Format | Example | Description |
|---|---|---|
resource:action | agents:read | Access all resources of a type |
resource:<id>:action | agents:my-agent:run | Access a specific resource |
resource:*:action | agents:*:read | Wildcard (equivalent to global) |
agent_os:admin | - | Full access to all endpoints |
Complete Scope Reference
Admin Scopes
| Scope | Description |
|---|---|
agent_os:admin | Full admin access to all endpoints |
System Scopes
| Scope | Description |
|---|---|
system:read | View system configuration and available models |
Agent Scopes
| Scope | Description |
|---|---|
agents:read | List and view all agents |
agents:write | Create and update agents |
agents:delete | Delete agents |
agents:run | Run any agent |
agents:<agent-id>:read | View a specific agent |
agents:<agent-id>:run | Run a specific agent |
Team Scopes
| Scope | Description |
|---|---|
teams:read | List and view all teams |
teams:write | Create and update teams |
teams:delete | Delete teams |
teams:run | Run any team |
teams:<team-id>:read | View a specific team |
teams:<team-id>:run | Run a specific team |
Workflow Scopes
| Scope | Description |
|---|---|
workflows:read | List and view all workflows |
workflows:write | Create and update workflows |
workflows:delete | Delete workflows |
workflows:run | Run any workflow |
workflows:<workflow-id>:read | View a specific workflow |
workflows:<workflow-id>:run | Run a specific workflow |
Session Scopes
| Scope | Description |
|---|---|
sessions:read | View all sessions and session data |
sessions:write | Create, update, and rename sessions |
sessions:delete | Delete sessions |
Memory Scopes
| Scope | Description |
|---|---|
memories:read | View memories and memory topics |
memories:write | Create, update, and optimize memories |
memories:delete | Delete memories |
Knowledge Scopes
| Scope | Description |
|---|---|
knowledge:read | View and search knowledge content |
knowledge:write | Add and update knowledge content |
knowledge:delete | Delete knowledge content |
Metrics Scopes
| Scope | Description |
|---|---|
metrics:read | View metrics |
metrics:write | Refresh metrics |
Evaluation Scopes
| Scope | Description |
|---|---|
evals:read | View evaluation runs |
evals:write | Create and update evaluation runs |
evals:delete | Delete evaluation runs |
Default Scope Mappings
AgentOS automatically maps endpoints to required scopes.- System
- Agents
- Teams
- Workflows
- Sessions
- Memories
- Knowledge
- Metrics
- Evals
| Endpoint | Required Scope |
|---|---|
GET /config | system:read |
GET /models | system:read |
Custom Scope Mappings
Customize or extend the default scope mappings using the JWT middleware:JWT Token Structure
Your JWT tokens should include:| Claim | Required | Description |
|---|---|---|
scopes | Yes | Array of permission scopes |
sub | No | User ID (extracted as user_id) |
session_id | No | Session ID for session tracking |
aud | No | Audience (must match AgentOS id when verify_audience=True) |
Example Tokens
Read-only access:Configuration Options
Configure JWT verification usingAuthorizationConfig:
Excluded Routes
These routes are excluded from RBAC checks by default:/, /health, /docs, /redoc, /openapi.json, /docs/oauth2-redirect
Error Responses
| Status Code | Description |
|---|---|
401 Unauthorized | Missing or invalid JWT token |
403 Forbidden | Insufficient scopes for the requested operation |